Today I'll show you how to utilize Traefik locally with Kubernetes ☸️ to publish services using route matching and middlewares in an excellent approach.
Requirements
We require K3s to run containers locally; if you want an introduction, I wrote the following articles:
We could also use minikube, but it didn't function well with Traefik when I tried to install CRDS and use middleware, so I'll look into it in another post.
Podman lover ❤️?
If you enjoy Podman, this is for you. Take a look after this post if you want to use podman instead of Kubernetes ☸️.
What is Traefik?
Traefik is a modern HTTP reverse proxy and load balancer developed in Go that is suited for microservice architecture. It is commonly used in containerized environments, such as Docker and Kubernetes.
Traefik dynamically detects services as they are introduced to the infrastructure and routes traffic to them, making applications easier to manage and grow.
Major features:
- Automatic Service Discovery: Traefik can detect new services as they are introduced to your infrastructure, removing the need for human configuration.
- Dynamic Configuration: It can reorganize itself as services scale up or down, making it ideal for dynamic contexts like as container orchestration platforms.
- Load Balancing: Traefik includes built-in load balancing capabilities for distributing incoming traffic over many instances of a service.
- Automatic TLS: It may supply TLS certificates from Let's Encrypt, enabling HTTPS by default without requiring manual configuration.
- Dashboard: Traefik includes a web dashboard and a RESTful API, which enable operators to monitor and manage traffic routing and configuration.
- Middleware Support: It supports a number of middleware plugins for features like authentication, rate limiting, and request rewriting.
- Multiple Backends: Traefik can route traffic to multiple backend services based on various criteria like path, headers, or domain names.
Goals 🎯
The goal is to create an example of using K3s to offer a node Kubernetes with Traefik; after provisioning, we will launch apps at ingress while enabling some Traefik middleware, demonstrating its true power 🔥.
K3s uses Traefik as the routing edge by default, so all you need to do is configure services and modify deployments.
🔥 Brace yourselves, deploy is coming...

Setting Up k3s with Traefik
Firstly, ensuring that K3s and Traefik are running:
Let us check to see whether pods are running properly.
Then let's check HTTP requests to Traefik; it should return 404 because there is no service routed at ingress.
Setting up local domains
Please adds to /etc/hosts file, the domains (whoami.local-k3s and traefik.local-k3s)
Deploying WhoAmI
Now it's time to set up a basic pod that I used in a previous post to respond to HTTP requests and allow us to understand how the Kubernetes ☸️ stack works.
Let's create some yaml files:
- whoami-middleware.yaml
This file defines a middleware that will be used in a Kubernetes service. The middleware adds a custom header to any request containing the header X-Origin.
- whoami-deployment.yaml
That file describes two components: Kubernetes ☸️ service and deployment. The pod uses port 80, and the service is the same, with only one replica.
- whoami-ingress.yaml
Here we apply the rules to ingress find our service; this match uses the host as a rule and applies the previously established middleware.
Now, let’s put these definitions into action!
Expected response:
If everything goes well, we will be able to connect to your service via host on port 80 http://whoami.local-k3s/.
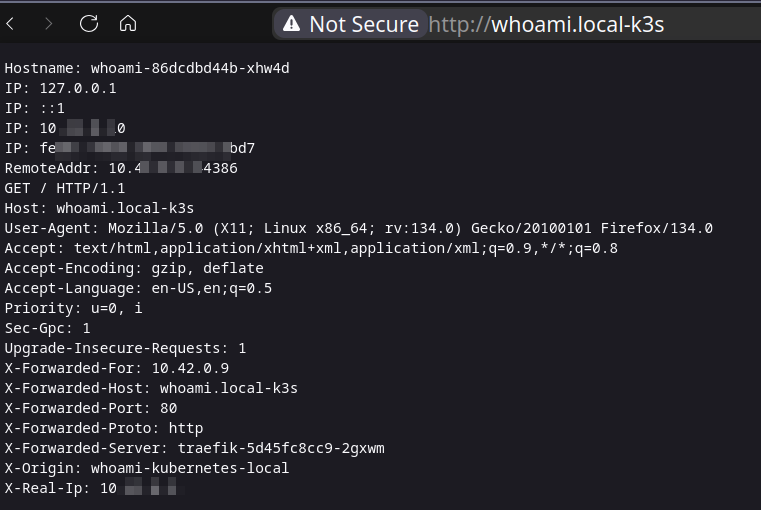
As we can see, when X-Origin is applied to a request, whoami returns all http request headers, which is great for testing 🚀.
Deploying the Traefik Dashboard
The Traefik Dashboard gives real-time visibility into your Kubernetes ☸️ ingress routes, services, and middleware. You may monitor active routes, examine the status of load balancing, and validate middleware setups such as authentication and header updates. It also lets you inspect TLS certificates, monitor backend health, and troubleshoot routing difficulties. You can improve security by protecting the dashboard with Basic Authentication or other access constraints.
Here I'll show you how to enable Traefik Dashboard. By default, there is no authentication, so it's not a good idea to enable at ingress without some security; my proposal is that this type of tool have limited access to a VPN or IP allow list.
Patch Traefik Services
K3s does not expose port 9000 at service, which is required for API and dashboard, therefore we need to patch.
- traefik-service-patch.yaml
The following command applies the patch to the Traefik service that is currently running:
Let's inspect the port listening:
The expected result:
We now need some files to route Traefik Dasboard across ingress in secure mode.
- traefik-auth-middleware.yaml
This file defines the middleware HTTP basic authentication.
- traefik-secret.yaml
We define the value of HTTP basic authentication, which represents user: foo and password: bar. Please do not use this in production 😂 since it is very powerful 💪.
- traefik-dashboard-ingress.yaml
As with the previous ingress route, the match is made by host and is now protected by middleware HTTP basic authentication.
It's time to put these definitions into practice!
Expected result:
Now we can access the Dashboard (http://traefik.local-k3s), but it is secured by the HTTP basic authentication credentials foo:bar.
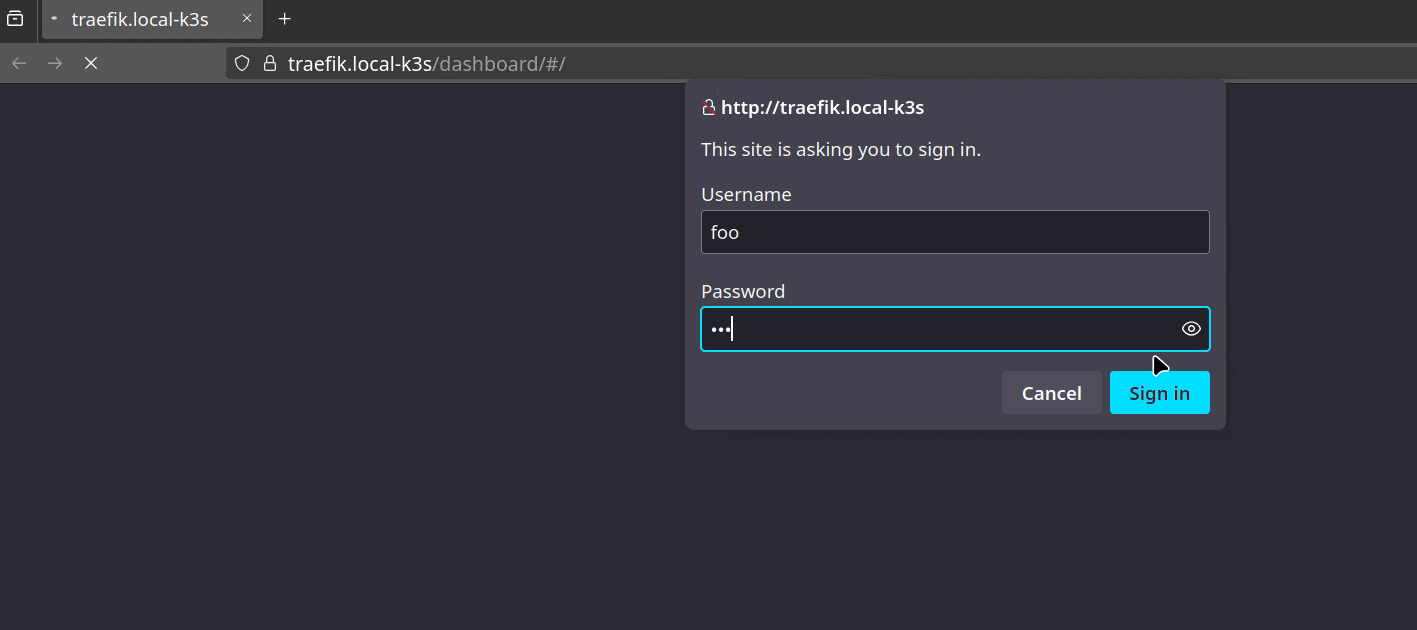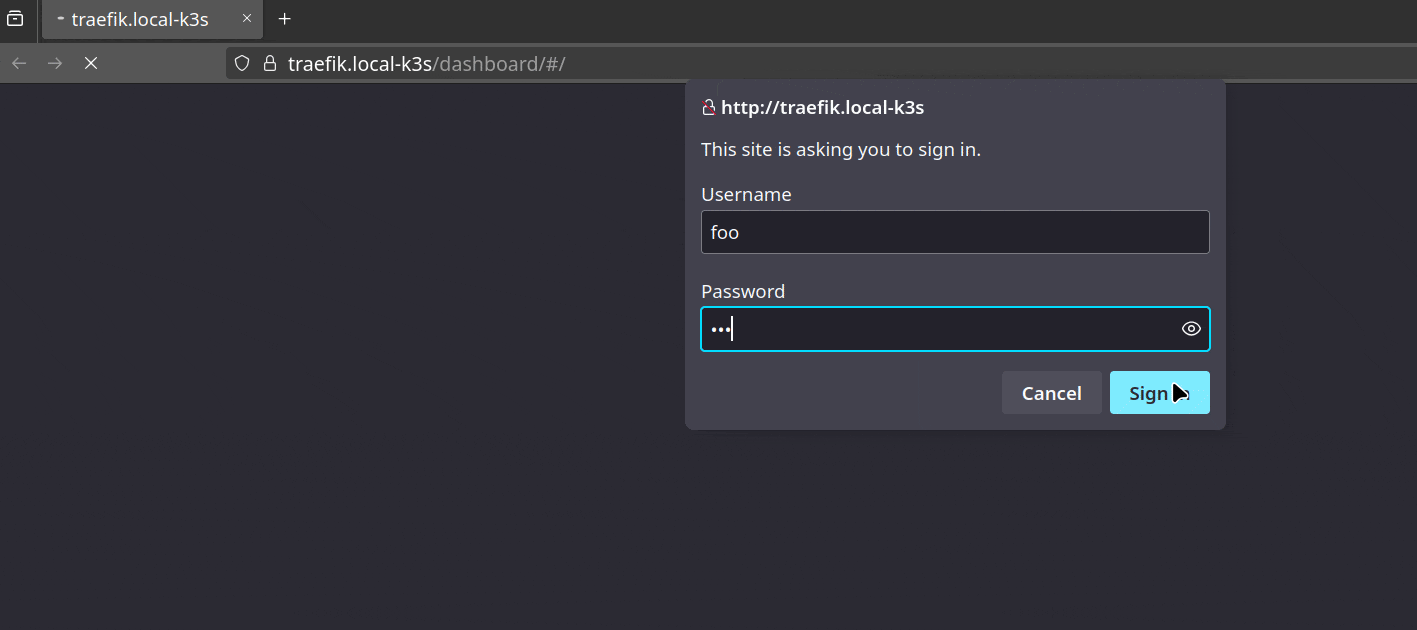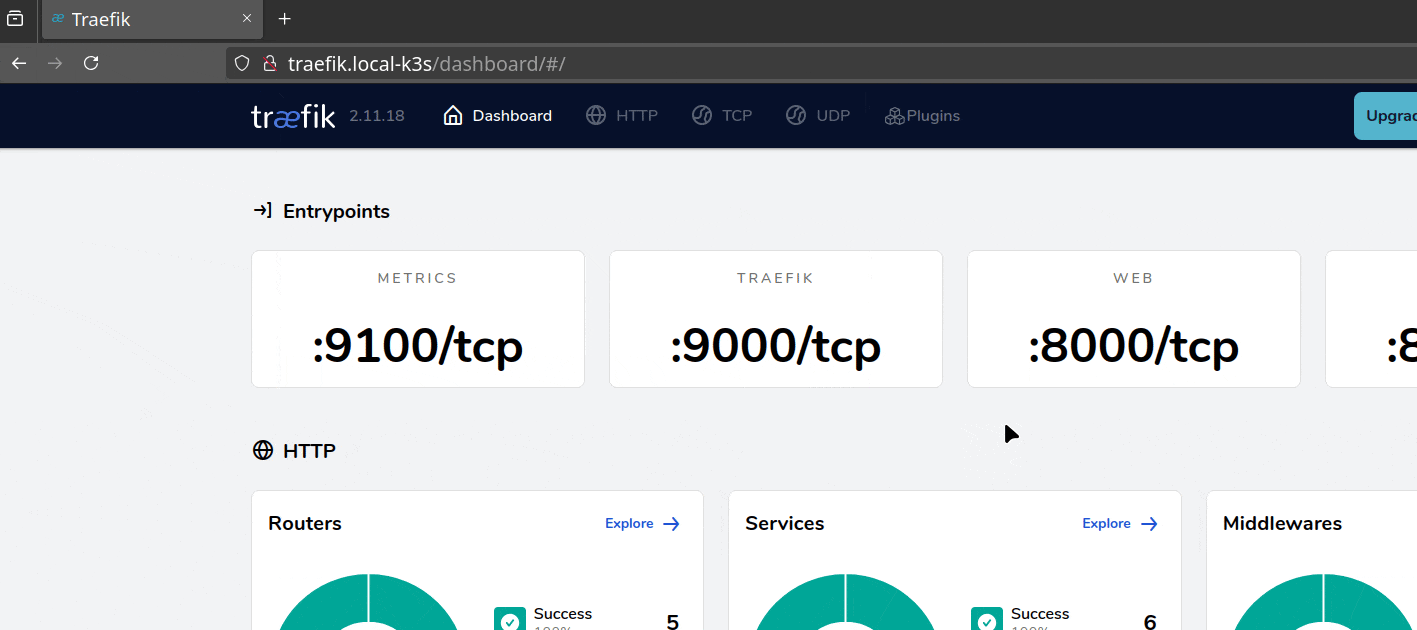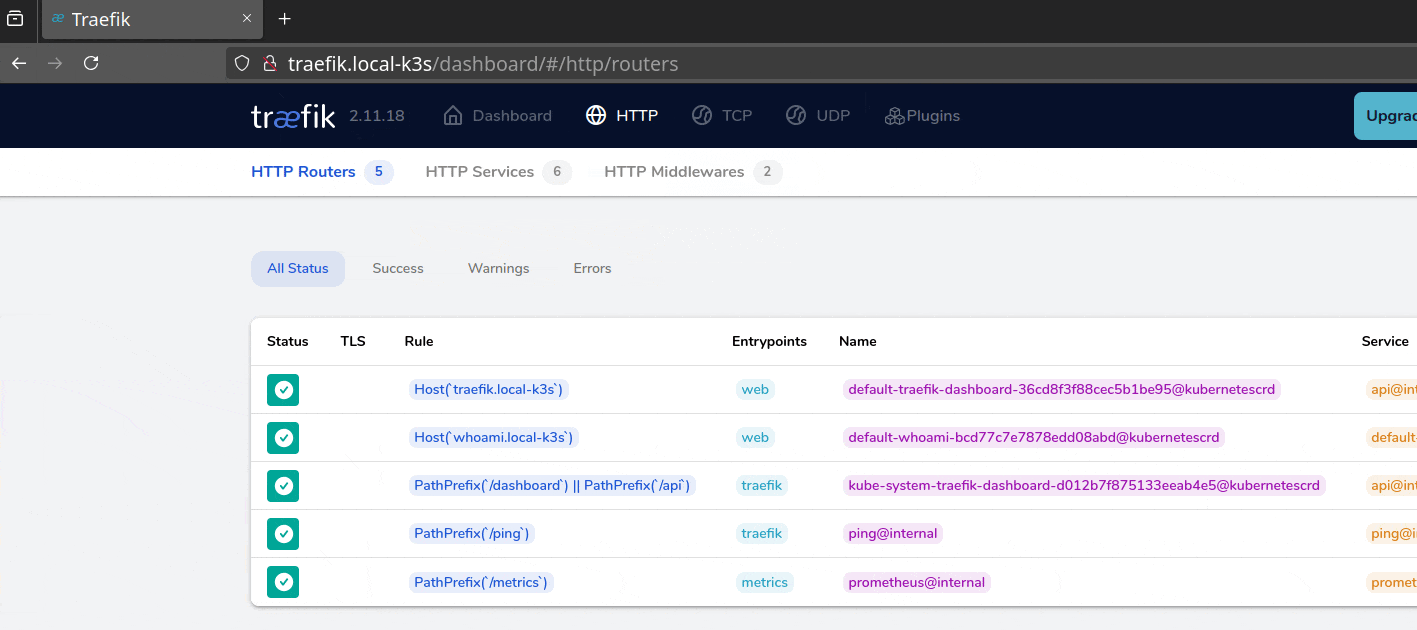
It works, but I would never propose making this access public; instead, use a VPN to protect yourself 🧐.
Another ways to enable Dashboard
Using forward
This method allows you to route the Traefik and access the dashboard at port 9000, but keep in mind that there is no authentication. This command is running in the foreground, therefore closing the terminal will cause the forward to stop.
Editing service to expose port 9000 (manually)
The following command will edit the service with a file, which is handy for local testing.
Adding these specifications, port 9000 will be listening:
Works, however there is no authentication, therefore it is not ready for production. 😉
Code
💡 Feel free to clone this repository, which contains related files:

That's all
In this post, we set up a Traefik-routed service over Ingress, and I demonstrate how to enable the Traefik dashboard in a variety of ways, the most significant of which is in a secure way, avoiding any issues caused by exposing your settings.
I hope this article helps you create your Kubernetes ☸️ stack with Traefik, and I'd love ❤️ to hear 👂 your questions or share your experiences, that's it.

Don't forget to upgrade your kernel 🧠; God bless 🕊️ you and your family.








